PROFINET Security - The Easy and Affordable Security Concept
When the first PROFINET specifications were issued, PI published a comprehensive security concept that was refined and improved in several stages. The same requirements apply now as they did then. Protecting plant networks and automation components is not enough; the protection mechanisms and concepts used must also not disrupt ongoing production operations. Additionally, protection concepts must be easy to implement and affordable.
Proven Concept
The security concept for PROFINET is based on a defense-in-depth approach. In this approach, the production plant is protected against attacks, especially from outside, by a combination of different protective measures. This includes firewalls as well as the communication protection of the PROFINET protocol.
In addition, further protection is possible within the plant by dividing the communication network into zones using firewalls. A security component test ensures that the PROFINET components comply to the standard and that they are resistant to defined overload conditions.
This concept is complimented by organizational measures in the production plant as part of an information security management system (ISMS). Security therefore requires measures at all levels.
Security Measures are Always Changing
Since every application has different security requirements, PROFINET offers different Security Classes.
See the following video for more information.
Secure Communication with PROFINET
Due to increased security needs, the cell protection concept for PROFINET alone is no longer sufficient. Additional measures need to be taken.
Focus on reliability and real-time
In the IT world, there are proven security concepts that also guide similar concepts in automation communication domain. However, PI’s analyses have shown that these concepts cannot simply be transferred to the automation world. For examples:
PROFINET devices are primarily geared toward reliability and real-time communication. Additionally, usability in an industrial environment plays an important role in technology design. Security functions, such as a certificate check, must be implementable in a practical manner. Additionally, in business IT, protection goals are sometimes prioritized differently, where confidentiality is an important asset. This plays a subordinate role in communication networks in automation technology.
Prioritization of Protection Targets
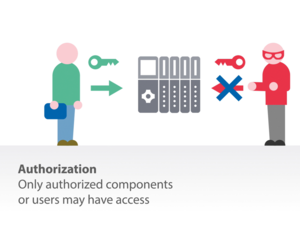
The IEC 62443 standard for industrial security forms the basis for of PI’s security concepts. In many automation systems, the following priorities are assigned to these goals, which may differ in individual cases and applications:
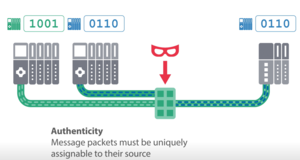
Authenticity (devices / users)
Authenticity ensures the unique identification of a system component and its data. Components must "identify themselves" and have a forgery-proof digital identity. Authorizations assigned to an authenticated user (software process or device) enable the user to perform required actions in the automation system, enforce these actions, and monitor their use.
Security Classes Related to PROFINET
Since the multitude of industries and applications also entails different security requirements, three security classes were introduced in PROFINET. This is because the requirement of 'confidentiality', for example, entails a very high computing time expenditure for encryption measures. However, this is not necessary in many applications.
Security Class 1 (robustness) generally provides for sealing off the system from the outside, segmentation of the production network, access protection, and other measures (Defense-in-Depth concept). This will now be extended inon some points. This includes the ability to change SNMP default strings, DCP commands can be set to "read only" and GSD files can be protected against unnoticed changes by signing.
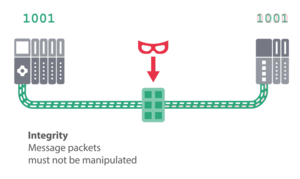
For Security Class 2 (integrity and authenticity), in addition to Security Class 1, the integrity and authenticity of PROFINET data communication, as well as the confidentiality of configuration data via cryptographic functions is specified. This is the case, for example, in systems that cannot be easily divided into zones or where access from the outside is not secured, such as outdoor installations.
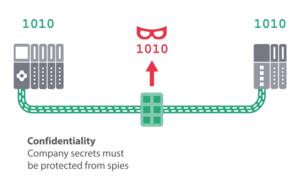
In Security Class 3, the confidentiality of PROFINET data is also specified. This is the case, for example, if company secrets can be inferred from this data.
Most applications will be able to work on the basis of Security Classes 1 and 2. The creation/checking of security information during protocol extension generally leads to an increase in component resources. Such integrity and authenticity checks must not have any effects on the performance of PROFINET.
Event Logging
Security is not just a question of prevention - it also requires continuous monitoring and documentation of security-relevant events. Event logging makes it possible to detect security-relevant processes in IT and OT systems, analyze them and initiate targeted countermeasures. In critical infrastructures in particular, this technology is indispensable for documenting threats such as unauthorized access, failed authentication or configuration changes and reacting to them in good time if necessary. The continuous recording of such events not only creates transparency, but also the basis for forensic analysis in the event of an attack. With the extensions to the PROFINET protocol, security event logging mechanisms have been specified as an integral part. The extension enables security-relevant events to be systematically recorded and forwarded to higher-level monitoring systems. This includes the detection of security-critical events.
Protective Measures in the PROFINET Communication Network
The PROFINET security concept is based on well-known and generally accepted cryptographic algorithms and protocols. However, flexible lifecycle management is required for security functions. This is important in case cryptographic algorithms can be assumed to be insecure or weaknesses in the concept are discovered. In addition, there are other aspects that must be considered for secure PROFINET communication:
- Ensuring the authenticity of PROFINET stations by means of a cryptographically secured digital identity in the form of certificates. The concept should include the possibility of securely storing this identity, e.g., in a specially secured hardware component in the respective station.
- Ensuring the integrity of communication by cryptographic measures, e.g. cryptographic checksums. This security should cover all communication channels of the PROFINET Device, including IP communication, PROFINET real-time communication, and communication for network management.
- Ensuring system startup and the assignment of components, e.g. from PROFINET Devices to PROFINET Controllers and engineering tools, by means of cryptographic measures. This also applies to a system startup after a connection termination.
- Reporting of security-relevant events that can be detected by PROFINET devices. For example, through additional PROFINET IT security alarms.
- Ensuring the confidentiality of acyclic data and configuration data. Additional assurance of confidentiality for cyclic data as an optional function in Security Class 3.
- Ensuring minimum resistance against denial-of-service attacks.
- Protection of the integrity and authenticity of General Station Descriptions (GSD files).
- Secured end-to-end communication between controllers and associated devices and optional integration of monitoring/diagnostic systems.
- Configuration option for machines with higher security requirements (different security profiles).
- Support and protection - as transparent as possible - of existing PROFINET profiles/functions, e.g. PROFIsafe.
Assuring Quality of Security Implementations
To ensure that manufacturers take sufficient account of the enhanced security requirements with regard to stack implementation, PI has started to expand the certification test for PROFINET to include PROFINET security test scenarios (including the security classes). The first test cases have already been integrated into the current version of the PROFINET Tester and are being tested by the PITLs.
PROFINET Test Bundle
PI has set up a Cyber Security Incident Response Team (CSIRT) to resolve potential security incidents. The PI-CSIRT provides information and support to member companies and users of PI technologies. This includes assistance in implementing proactive measures to reduce the risk of security breaches and to respond to such breaches or incidents as soon as they occur by analyzing the incidents and publishing security advisories.
Roles and Responsibilities
| PI | Manufacturers | Users | |
|---|---|---|---|
| Responsibilities | Develop and maintain security specifications, guidelines, and best practices. Provide Test System for certification | Implement security measures in devices and systems. | Follow security guidelines and best practices for device usage and provisioning. |
| Expectations | Ensure that device manufacturers and users adhere to (security) guidelines. | Provide documentation and support for device security features. | Keep devices and systems up to date with security patches. |
| Challenges |
| Keeping pace with evolving threats and attacks. | Awareness or understanding of security best practices |
The Differences in Security Classes
The different security classes also require different efforts by the device manufacturers for implementation in the devices and by the users for integration into their systems and machines.
Handling of Certificates
Authentication is based on certificates, both for devices and operators. The handling of certificates is required in Security Class 2 and 3. Authentication via username/password is not planned. The PROFINET Certificate Management handles the initial provision of certificates as well as the renewal/updating and revocation. Key generation is supported by devices as well as external sources (e.g. tools).
Handling of GSDs
The integrity and authenticity of GSD files must be ensured. For example, manufacturers must be able to digitally sign their GSD files as an optional security extension. Individual provider-specific certificates can be requested from the PNO. The engineering system will validate the GSD signature during import. This creates trust in the GSD configuration data. A user guide with details (about all Class 1 features) and the GSDX-Spec are available.
Here you can find several frequently asked questions:
Parallel operation of secured and unsecured connections in an IO system and also in existing network infrastructure (e.g. switches) is possible.
The beginnings of the international series of standards IEC 62443 are roughly 20 years old and specify a holistic security approach for operators, integrators, and device vendors. The IEC 62443 is the accepted international series of standards on "Industrial communicationnetworks - IT security for networks and systems". The standards can be divided into four areas:
- The first area describes basic concepts such as Defense-in-Depth, basic security requirements, and then refers to the other parts of the standard for concrete implementation.
- A further area defines guidelines and guides for the implementation of organizational measures and gives recommendations.
- The third part describes technical aspects such as security levels and security requirements.
- The fourth part is aimed specifically at the product and component view (sensors, interfaces, chips, etc.) and is therefore more aimed at device vendors.
PROFINET Security Guideline
The Security guideline points out the key aspects for the establishment of a security concept in an industrial environment and provides appropriate recommendations. This guideline (Order. No. 7.001, 7002) dates November 2013. It will be replaced by an updated guideline that considers the PROFINET security concept as well as the requirements of the IEC 62443.
PROFINET Security Class 1 Guideline
This document is intended to provide an overview of the planed methods, applications and processes of the PROFINET Security extension in Security Class 1. It addresses component manufacturers, system vendors, and users of PROFINET technology.
Read more
PI White Paper: OT-Security - Classification of IEC62443
This white paper first provides an overview of the various parts of the IEC 62443 series of standards and briefly describing their contents. Next, it assigns the standard parts to the stakeholders in the OT security process. In the field of Operational Technology (OT) these include plant operators, system integrators and the product suppliers. Building on these front-up considerations, the document maps the security concept of PROFINET to the different parts of the IEC 62443.
Read more
IT security extensions for PROFINET
Karl-Heinz Niemann
This paper was presented at the IEEE 17th International Conference on Industrial Informatics (INDIN) in 2019. It gives an overview of the concepts of PROFINET security.
Read more
Security extensions for PROFINET - Concepts, Status and Prospects
Karl-Heinz Niemann, Andreas Walz, Axel Sikora
This paper was presented at the Embedded World 2023 Exhibition & Conference 2023. It describes the technological concepts of PROFINET security.
A Mechanism for Seamless Cryptographic Rekeying in Real-Time Communication Systems
Heiko Bühler, Andreas Walz, Axel Sikora
The paper was presented at 17th IEEE International Conference on Factory Communication Systems (WFCS) in 2021. The document presents a novel seamless rekeying approach, which can be embedded into cyclic application data exchanges. Although, being agnostic to the underlying real-time communication system, the developed demonstrator can emulate the widespread industrial Ethernet system PROFINET IO and successfully use this rekeying mechanism.
PROFINET Security: A Look on Selected Concepts for Secure Communication in the Automation Domain
Andreas. Walz, K.-Harl-Heinz. Niemann, Julian. Göppert, K. ai Fischer, S. imon Merklin, D. ominik Ziegler, Axel. Sikora
The paper was published at the IEEE 21st International Conference on Industrial Informatics (INDIN) in 2023. It provides a brief overview of the cryptographic security extensions for PROFINET, as defined and specified by PROFIBUS & PROFINET International (PI)
How to develop a secure PROFINET device: Organizational and technical OT security measures during the development of PROFINET devices
Karl-Heinz Niemann, Andreas Walz,, Simon Merklin, Andreas Ziegler, Boris Waldeck
This article was originally published in the atp magazine 09/2023. The article shows which technical and organizational measures have to be considered during the development of a PROFINET device supporting PROFINET security. An Ethernet APL transmitter serves as an example. Based on that analysis, requirements for the secure design of Ethernet APL communication combined with PROFINET are derived from.
OT Security Requirements for Ethernet-APL field devices
Karl-Heinz Niemann, Simon Merklin
This paper was published in the atp magazine 05/2022. It describes cyber security attack scenarios for automation systems using current loop with HART, PROFIBUS PA and Ethernet APL in combination with PROFINET.
Cryptographic Protection of Cyclic Real-Time Communication in Ethernet-Based Fieldbuses: How Much Hardware is Required?
Matthias Skuballa, Andreas Walz, Heiko Bühler, Axel Sikora
This paper was presented at 26th IEEE International Conference on Emerging Technologies and Factory Automation (ETFA ) in 2021. It evaluates the performance of or the EAS-GCM Algorithm that is used for PROFINET security.